We can’t keep ignoring privacy threats lurking within iPhones and Android devices
As more apps conspire to steal your data, it’s time for all users of technology to become more vigilant

We live in an age of truly amazing technology. Today’s smartphones can be a window into all human knowledge and media, along with providing access to quite literally every LOLcat that currently exists on the internet.
But as modern technology barrels along, evolving at breakneck pace, people’s ability to adapt to threats simply isn’t keeping up.
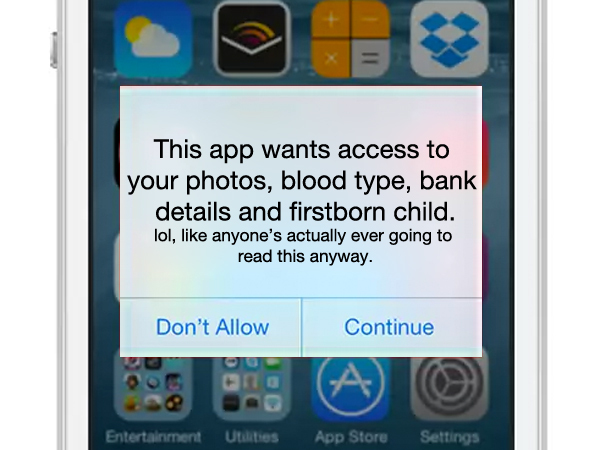
Perhaps the biggest change in technology we’ve seen in recent years is an overt shift to computing devices as appliances. Whereas in the early 1980s, you’d have sat there in front of a command line, in relatively full control of a machine, now you’re often almost reduced to an automaton, a component of a flesh/smartphone cyborg, prodding at a glass screen as apps attempt to worm their way into your data. Increasingly, we’re asked to make very important decisions that may require involved thought or investigation, but that can effectively be dismissed by tapping a tempting OK button.
READ MORE: Everything you need to know about the Google Nexus 6
It’s hard to know what the core of the problem is. It’s easy to argue ignorance or outright stupidity, but that’s entirely unfair on people who aren’t proficient with technology, and it veers far too close to victim-blaming when things happen to go wrong. Weariness is certainly a part of it, though – the net result of the constant micromanagement that now comes with owning a mobile device; it’s often too easy to just hit OK a bunch of times to make something be quiet and go away, in order to get yourself some peace.
Mostly, though, it seems that as technology’s transformed itself and developed a friendlier face, people are simply more likely to be more trusting. When an app installs, your first thought isn’t that it might be designed to perform nefarious tasks; when a product wants to integrate with your existing data, your first thought isn’t that it’s performing social engineering, aiming to get at your data, and perhaps send it on to a repository in one of the seedier corners of the internet.
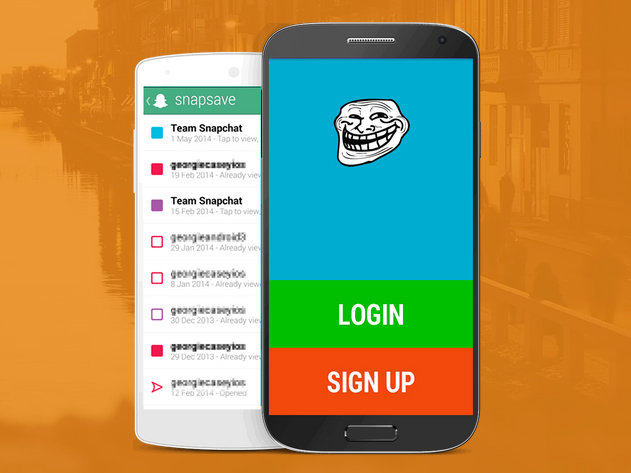
And yet recently we’ve again seen the damage mobile apps can do. Reports showed many people integrated Snapchat with a third-party site called snapsaved.com, which promised to save their pictures to the desktop, rather than have them vanish seconds after arrival; instead, it got hacked and hundreds of thousands of their photos are now in the hands of unscrupulous ‘hackers’, and are in the process of being leaked online.
READ MORE: New iPads! New Macs! No U2! What to expect from Apple’s 16 October event
Further ramming home how absurd things have gotten, Snoopwall issued a flashlight apps threat assessment report earlier this month. The gist was that although flashlights only really need permission to access a device’s flash and screen, many treat a device as a free-for-all, asking for permission for network access, GPS, status bar modification, vibration control, Wi-Fi connection viewing, and more.
The 10 flashlight apps assessed by Snoopwall may together have had more than half a billion installs. While there’s no suggestion that any of these apps are actually abusing those permissions, it’s tempting to wonder how many people even considered that they might have done. How many people denied them access to critical system components and data? And how many were just accepting of the apps, trusting them, or quick to dismiss the lists of permissions because they were a momentary inconvenience?
And before you scoff at how you’d of course never allow that to happen to you, are you sure? How many services you don’t really know well are linked to your Twitter or Facebook account? How many apps where you in reality know nothing about the developer have access to your contacts, your photos, and more?
Technology will only become more ubiquitous as time moves on, melting further into the background, and becoming increasingly invisible. As it does so, our acceptance of it – our trust in it – must be countered by a layer of suspicion and investigation. If an app or a website wants something from you, question why. And if you’re not convinced, don’t tap OK – tap Cancel and then delete.
READ MORE: Why you shouldn’t celebrate CD-ripping finally becoming legal in the UK